Chris Mark Speaking at 2014 AT&T CyberSecurity Conference August 25, 2014
Posted by Chris Mark in Uncategorized.Tags: adaptive, AT&T, Chris Mark, cyber, deterrence, hack, PCI, risk, security, threat
add a comment
 At 10 am on September 3rd, 2014 Chris (that is me) will be speaking at the 16th annual AT&T CyberSecurity Conference in New York City. My particular discussion will be on the Human Element of Security. From providing armed force protection in Mogadishu to unarmed security in a psychiatric ward through information security and anti-piracy work in the Gulf of Aden, I have learned that the underpinnings of security transcend all security domains. My presentation will hit on the concepts of rationality, Knightian uncertainty, parallax, proximate reality, change blindness, deterrence, and threat adaptation to provide tools CSOs can use to make more informed decisions about security.
At 10 am on September 3rd, 2014 Chris (that is me) will be speaking at the 16th annual AT&T CyberSecurity Conference in New York City. My particular discussion will be on the Human Element of Security. From providing armed force protection in Mogadishu to unarmed security in a psychiatric ward through information security and anti-piracy work in the Gulf of Aden, I have learned that the underpinnings of security transcend all security domains. My presentation will hit on the concepts of rationality, Knightian uncertainty, parallax, proximate reality, change blindness, deterrence, and threat adaptation to provide tools CSOs can use to make more informed decisions about security.
Chris Mark in July 2014 of TransactionWorld (Proximate Reality) July 1, 2014
Posted by Chris Mark in cybersecurity.Tags: adaptive, Breach, Chris Mark, cyber, decision science, proximate reality, security, threats
2 comments
 July’s issue of TransactionWorld Magazine was just released. Click here to read my latest article, “Understanding Proximate Reality to Improve Security” Here is a preview..
July’s issue of TransactionWorld Magazine was just released. Click here to read my latest article, “Understanding Proximate Reality to Improve Security” Here is a preview..
“Various reports are published annually that analyze data breaches, opine on the root causes of the data theft and frequently ascribe blame to one party or another. It always invites scrutiny when a well-known security firm or analyst makes a definitive statement such as “X% of breaches could have been prevented through the implementation of basic controls, such as patching.”
This position is not only inconsistent with accepted risk management practices, but also confuses the basic concepts of correlation and causation while ignoring the very human element of adaptation. Unfortunately, companies that subscribe to these simplistic views of the industry and threats are exposing themselves to very real dangers. As supported by the increasing number of breaches identified each year, information security is no longer a domain for amateurs and requires the application of lessons learned from domains such as intelligence, anti-terrorism, and decision science to make effective decisions.
Two important concepts borrowed from the intelligence and anti-terrorism domains can be used to help CSOs and others make relevant decisions related to their risk posture and other aspects of data security. These concepts are known as Proximate Reality and Adaptive Threats.” Read More!
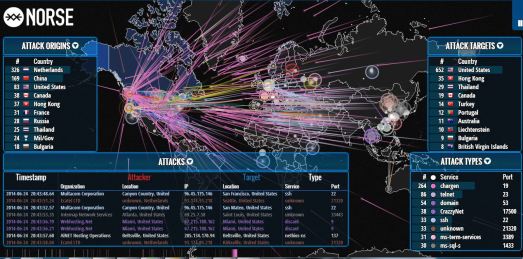
Norse- Live Cyber Threat Intelligence (very cool!) June 24, 2014
Posted by Chris Mark in Uncategorized.Tags: attack, cyber, espionage, hack, IPViking, Norse, threat, vulnerability
add a comment
I have been thinking about a topic on which to write. I recently ran across this company called Norse and was impressed by the live cyber intelligence Norse provides. Please checkout their website…as stated: “Every second, Norse collects and analyzes live threat intelligence from darknets in hundreds of locations in over 40 countries. The attacks shown are based on a small subset of live flows against the Norse honeypot infrastructure, representing actual worldwide cyber attacks by bad actors. At a glance, one can see which countries are aggressors or targets at the moment, using which type of attacks (services-ports). “…forgive the language but this is…badass!