Chris Mark Speaking at 2014 AT&T CyberSecurity Conference August 25, 2014
Posted by Chris Mark in Uncategorized.Tags: adaptive, AT&T, Chris Mark, cyber, deterrence, hack, PCI, risk, security, threat
add a comment
 At 10 am on September 3rd, 2014 Chris (that is me) will be speaking at the 16th annual AT&T CyberSecurity Conference in New York City. My particular discussion will be on the Human Element of Security. From providing armed force protection in Mogadishu to unarmed security in a psychiatric ward through information security and anti-piracy work in the Gulf of Aden, I have learned that the underpinnings of security transcend all security domains. My presentation will hit on the concepts of rationality, Knightian uncertainty, parallax, proximate reality, change blindness, deterrence, and threat adaptation to provide tools CSOs can use to make more informed decisions about security.
At 10 am on September 3rd, 2014 Chris (that is me) will be speaking at the 16th annual AT&T CyberSecurity Conference in New York City. My particular discussion will be on the Human Element of Security. From providing armed force protection in Mogadishu to unarmed security in a psychiatric ward through information security and anti-piracy work in the Gulf of Aden, I have learned that the underpinnings of security transcend all security domains. My presentation will hit on the concepts of rationality, Knightian uncertainty, parallax, proximate reality, change blindness, deterrence, and threat adaptation to provide tools CSOs can use to make more informed decisions about security.
Chris Mark speaking on PCI at a Business Process Outsourcing (BPO) event 2013 June 29, 2014
Posted by Chris Mark in Uncategorized.Tags: AT&T, Chris Mark, compliance, compromise, data breach, DSS, hack, PCI, risk, security
2 comments
I was privileged to be able to speak at an AT&T BPO event in 2013. In Feb 2014 AT&T Marketing published the videos. I found one but was unaware they had published all 3. I hope you enjoy. (remember…the camera adds 10 lbs! 😉
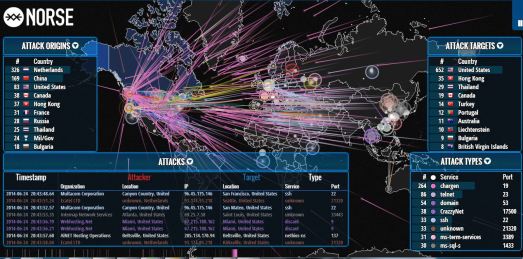
Norse- Live Cyber Threat Intelligence (very cool!) June 24, 2014
Posted by Chris Mark in Uncategorized.Tags: attack, cyber, espionage, hack, IPViking, Norse, threat, vulnerability
add a comment
I have been thinking about a topic on which to write. I recently ran across this company called Norse and was impressed by the live cyber intelligence Norse provides. Please checkout their website…as stated: “Every second, Norse collects and analyzes live threat intelligence from darknets in hundreds of locations in over 40 countries. The attacks shown are based on a small subset of live flows against the Norse honeypot infrastructure, representing actual worldwide cyber attacks by bad actors. At a glance, one can see which countries are aggressors or targets at the moment, using which type of attacks (services-ports). “…forgive the language but this is…badass!
“Failed State of Security” Part II; Cybercrime Victim Blaming May 18, 2014
Posted by Chris Mark in Uncategorized.Tags: causality, cause, Chris Mark, compromise, crime, cybercrime, data breach, deterrence, hack, PCI DSS, security, Target, theft, victim blaming, victimization
add a comment
 I am proud to release another research brief that is Part II of my “Failed State of Security” series in which I discuss and analyze victim blaming in the context of data security. In 2012 I published a research brief titled “A Failed State of Security: A Rational Analysis of Deterrence Theory and The Effect on CyberCrime.” in which I discussed the failing of law enforcement, and cybersecurity to deter cyber events and discussed the theory of deterrence and the need for deterrence within cybersecurity. You can download the article on IDGA’s website or on my own website here. This paper is part II of the “Failed State of Security” series. Started after the Target data breach, this topic is one that has always been close to me. In April 2009 I wrote an article titled “Lessons from the Heartland Breach” which was published as the cover story by TransactionWorld magazine.
I am proud to release another research brief that is Part II of my “Failed State of Security” series in which I discuss and analyze victim blaming in the context of data security. In 2012 I published a research brief titled “A Failed State of Security: A Rational Analysis of Deterrence Theory and The Effect on CyberCrime.” in which I discussed the failing of law enforcement, and cybersecurity to deter cyber events and discussed the theory of deterrence and the need for deterrence within cybersecurity. You can download the article on IDGA’s website or on my own website here. This paper is part II of the “Failed State of Security” series. Started after the Target data breach, this topic is one that has always been close to me. In April 2009 I wrote an article titled “Lessons from the Heartland Breach” which was published as the cover story by TransactionWorld magazine.
Victim blaming is common in sexual assault, as well as other types of crimes. A quick Internet search will demonstrate scores of instances in which the victim of a violent is blamed for being victimized. When we include a large, corporate entity it becomes easier to point the accusatory finger at the organization. Whether due to Schadenfreude or some other reason, people want to blame companies that are victimized by hackers. Did the company “cause” the breach? Were they somehow complicit in the attack? What do we mean when we say “cause”? What is a causal fallacy? These, and many more topics, are discussed in Part II of the “Failed State of Security” series. I invite you to download “Failed State of Security Part II”; Victim Blaming in Cybercrime. As always, I welcome any comments or debate on the topic…