Black Swans, Probability Ignorance & FUD: Risk 101 February 13, 2012
Posted by Chris Mark in Risk & Risk Management.Tags: Chris Mark, InfoSec & Privacy, Maritime Security, mark consulting group, markconsultinggroup.com, Piracy & Maritime Security, risk management, security, security theater
add a comment
 I have written several posts on risk and risk within the maritime security industry. You can read them here (#1, #2) There is a common mistake people sometimes make when venturing into risk management. It is the focus on the impact of an event while ignoring the probability or overestimating the probability of the event. Very serious events with very low probabilities of occurrence (or those which you are unable to calculate) are what has been coined as Black Swan events by Nassim Taleb in his book of the same name. When calculating or estimating risk it is sometimes a temptation to look at those incidents with high impact potential and low probabilities while ignoring the less severe events with her probability. This would be akin to venturing into the Amazon Rain Forest and protecting yourself from Grizzly bears (very large impact but low, low probability) only to die of blood loss from being bitten by a million mosquitoes because you did not take a mosquito net or bug spray as you were not concerned with “a little mosquito bite”.
I have written several posts on risk and risk within the maritime security industry. You can read them here (#1, #2) There is a common mistake people sometimes make when venturing into risk management. It is the focus on the impact of an event while ignoring the probability or overestimating the probability of the event. Very serious events with very low probabilities of occurrence (or those which you are unable to calculate) are what has been coined as Black Swan events by Nassim Taleb in his book of the same name. When calculating or estimating risk it is sometimes a temptation to look at those incidents with high impact potential and low probabilities while ignoring the less severe events with her probability. This would be akin to venturing into the Amazon Rain Forest and protecting yourself from Grizzly bears (very large impact but low, low probability) only to die of blood loss from being bitten by a million mosquitoes because you did not take a mosquito net or bug spray as you were not concerned with “a little mosquito bite”.
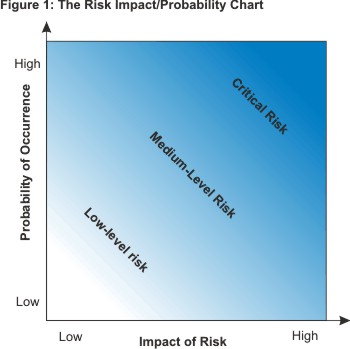
It is important to calculate risk by using a method that accounts for both impact and probability. This will give you a method by which to calculate the actual risk of an event and take appropriate steps to manage the risk. As can be seen by the graphic at the top of the post, a high impact low probability event poses the same risk as a low impact, high probability event assuming the ratios are equal. While the impact can be calculated as someone finite (for example, the worst that can happen to a person is likely to be killed) the probability of an event which can cause the event can range from unlikely to infinitesimally small. As an example of probability ignorance I will use an example from my own life. A woman I know carries a hammer in her car given to her by her mother. The purpose of the hammer is to break the car window and escape in the event the car plunges into a lake or other body of water and begins to sink. While the idea of drowning in a sinking car is certainly frightening, the likelihood of a car plunging into a body of water at 7,000 feet in high desert is very, very, very low. In this scenario it would be suggested that a better use of the money spent on the hammer was a 20 minute discussion on the value of always buckling the seatbelt and never speeding.
So why is this important? Simple. Security practitioners sell on a concept known as FUD or Fear, Uncertainty, and Doubt. A great example of FUD is a commercial I saw recently. A security company announced that 4 houses are burglarized every 14 seconds in the US. The commercial then goes on to show a mother and her children and how scary a burglary can be. Lets do some quick math to see how ‘scary’ this really is. According to the US Census Bureau there are about 131 million housing units in the US. If there is a house burglarized every 14.6 seconds this means that there are 4.1 burglarized per minute, 246 per hour, 5,917 per day and 216,000 per year. WOW! That is alot! BUT…this means that if you live in a home you have a .16% change of having your home burglarized in a given year. This does not seem so bad now. Keep in mind that some areas such as urban areas have higher crime rates than other areas and some houses are burglarized more than once. Another area where the security vendor attempts to convince you to use their services is by intimating that burglaries result in physical assault. In the commercials, a woman (not a man) is with her children talking about how the neighbor was burglarized and “while the children weren’t home, imagine if they had been.” Very few burglaries result in any physical harm to anyone but the imagery in the commercial is significant.
When listening to the inevitable sales pitch from a security vendor, keep in mind that they have an objective to sell you services. The easy way to do this is to use the FUD technique. If I am selling meteorite insurance, I will tell you about the dangers of meteorites, irrespective of who small they may be. Remember, it is easy to lie with numbers and easier to lie with statistics. Always base security implementation on a risk analysis.
Black Swan events – The Amazon rain forest example gives us a good opportunity to talk about Black Swan events. While we can calculate the probability of being attacked by a Grizzly bear in the Amazon (practically zero since they do not live anywhere but North America) there could be a situation in which a Grizzly bear was present and did attack someone. Maybe a person illegally imported a bear and let it go in the Amazon. This type of event would be a ‘Black Swan’ as you really could not calculate the probability of that specific event. The book is a very good starting point for this concept.
-Graphic from MindTools.com
“Slicing the Pie”; Risk Management 101 February 11, 2012
Posted by Chris Mark in Risk & Risk Management.Tags: black swan events, Chris Mark, combating piracy week, cybersecurity, data security, mark consulting group, markconsultinggroup.com, Risk & Risk Management, risk management, security
add a comment
 This is a followup to “Risk 101: an Introduction to Risk” Security, and Risk are interesting topics that lend themselves to endless debate (and the occasional argument). They are concepts that are bandied about quite frequently but, in my experience, are often not well understood by those using the terms. I have been asked by clients to describe risk management and security in business terms. At the risk of over simplifying the concepts, I will explain the concepts in this post. Security can be described rather simply as the implementation of controls to counter address a vulnerability or address a threat. Consider your house as an example. If you install a lock on the front door, you are implementing a control (the lock) to address a vulnerability (an unlocked door) and a threat (that an unauthorized person will enter).
This is a followup to “Risk 101: an Introduction to Risk” Security, and Risk are interesting topics that lend themselves to endless debate (and the occasional argument). They are concepts that are bandied about quite frequently but, in my experience, are often not well understood by those using the terms. I have been asked by clients to describe risk management and security in business terms. At the risk of over simplifying the concepts, I will explain the concepts in this post. Security can be described rather simply as the implementation of controls to counter address a vulnerability or address a threat. Consider your house as an example. If you install a lock on the front door, you are implementing a control (the lock) to address a vulnerability (an unlocked door) and a threat (that an unauthorized person will enter).
Risk can be described as the function of the likelihood of an event occurring and the impact should it occur. Risk can be quantified using a simple formula (R=P% x I$) or expressed qualitatively. In the scenario used above, there is a risk that your house will be burglarized. Depending upon where you live, and other factors, the likelihood (expressed in terms of probability) will vary from unlikely to more likely to very likely. The impact of the burglary will be determined by, among other things, the value of the assets that can be stolen. So how does this relate to security? The concepts are (or should be) inextricably entwined.
Controls should be implemented commensurate with the identified risk.
This is a very important concept. Consider the following scenario. If I were to offer you $1,000 to either 1) install a burglar alarm in your house or 2) install a fence to keep lions out of your yard, which option would you choose? Likely most readers would respond with the statement; “it depends upon where I live”. This demonstrates the example of security and risk management. There are two risks we are considering in this scenario. First, is the risk of burglary and second is the risk of lion attacks. If you live in the Kenyan bush, you may be more concerned about Lions as the probability is likely higher of a lion entering the yard then of a burglar. If you live in New York City you are likely more concerned about burglaries than lions as lions are not found in NYC (at least not legally). The controls you are considering are either a lock (to address the issues described previously) or a fence to address the threat of a lion entering the yard. Additionally, when we talk about ‘commensurate with the risk’ it means that the controls should be enough to address the risk but not too great. You would not put a $1,000 alarm system on a $500 car. It simply does not make sense and is an inefficient use of your limited resources.
With those topics covered very briefly, how do we discuss risk management from business terms? Easy. Consider that the risks to which you or your business are exposed are infinite. You may not believe there is a risk of being hit by a meteorite but I can assure you that as infinitesimally small as the chance may be, there is a chance (probability) and the impact is likely not very good (injury or death). If you question the example, read about the Sylacaugqa Meteorite here.
Now consider that the resources at your disposal (man hours, money, expertise, technology, information) is finite. You may have a huge budget, and world class expertise but the fact remains that you have finite resources to address infinite risks. The goal of risk management is to slice the pie of resources in a manner that allows you to address the greatest risks in the most efficient and effective manner possible. There are four primary methods of risk mitigation; Avoidance, Reduction, Sharing, and Retention or Acceptance. Using the burglary example.
Avoidance– You can ensure you don’t own anything that could be stolen. Or you could live in an isolated area where nobody else lives.
Reduction– You can reduce the risk (by reducing probability or impact) by installing locks or using a safe to protect your assets.
Sharing– You can get insurance for your assets to reimburse you if they are stolen.
Acceptance– you can simply accept the fact that burglary is a possibility but one you are willing to accept if the likelihood is remote or you have no assets to steal.
The idea is to allocate the pieces of pie (which represents your finite resources) in a manner to address as much of the risk as possible. It should be noted that there will always be residual risk and the possibility of Black Swan events.
Why Regulation Cannot Prevent CyberCrime (TransactionWorld) February 6, 2012
Posted by Chris Mark in InfoSec & Privacy, Laws and Leglslation, Risk & Risk Management.Tags: Chris Mark, cybercrime, cybersecurity, InfoSec, Maritime Security, risk management, security, transaction world
add a comment
 As the maritime industry is increasingly focused on protection of data assets, I thought it would be beneficial to include an article on the topic. This article is one I wrote for TransactionWorld in July, 2011. It is titled: “Why Regulation Cannot Prevent CyberCrime” and is a continuation on the discussion of the impact of deterrence on behavior.
As the maritime industry is increasingly focused on protection of data assets, I thought it would be beneficial to include an article on the topic. This article is one I wrote for TransactionWorld in July, 2011. It is titled: “Why Regulation Cannot Prevent CyberCrime” and is a continuation on the discussion of the impact of deterrence on behavior.
“Data security and privacy regulation have increased significantly over the past 10 years. The U.S. now has 46 state breach notification laws and there have been numerous bills introduced in Congress that propose to regulate personally identifiable information and to dictate security of such data. In spite of this increasing regulation, data breaches continue to plague the industry. Some have proposed that more regulation is the answer. Unfortunately, regulation alone is inadequate to prevent data theft and protect data.
At its core, data theft and network intrusions are crimes. At the risk of oversimplifying the work of criminologists, crime prevention can be summarized as using deterrents to affect protection of assets and prevention of theft. Protection applies to the ‘hardening’ of targets by implementing controls that increase the level of difficulty of perpetrating a crime. A vault is a good example of a protective measure. While no vault is completely impenetrable, vaults do provide significant protective value. Data security controls are protective measures. They are designed solely to limit attempts to obtain the target of value. Without a deterrence effect, criminals are free to attack companies at will without fear of retribution. This article will explore the value of deterrence in the prevention of crime.” (read full article here)
Chris Mark Speaking at Combating Piracy Week in Hamburg February 2, 2012
Posted by Chris Mark in Industry News, InfoSec & Privacy, Piracy & Maritime Security, Risk & Risk Management.Tags: Chris Mark, combating piracy week, cyberpiracy, hanson wade, InfoSec, Maritime Security, Piracy & Maritime Security, risk management, security
add a comment
I will be speaking at the Combating Piracy Week in Hamburg, Germany on the topic of CyberSecurity & CyberEspionage The topic will discuss the topics with a focus on who is trying to steal your data and why. It will also cover the technologies and tactics of how they can steal your corporate data and what the uses of such data. You can get a preview of the topic by reading the Maritime Executive article in which I was interviewed.
If you have not attended one of the Hanson Wade Piracy events, it is worth attending. Hanson Wade’ personnel do a great job of coordinating networking and the speakers are all very professional and very adept. I have had opportunity to speak at nearly 100 events in the past 12 years or so and I would put the Hanson Wade events in the top 5 in terms of value for the money. I highly recommend this event for security companies that want to meet decision makers and speak with the people who influence the industry from a security perspective.
A Rant about Risk- Rock Climbing with a 2 year old January 31, 2012
Posted by Chris Mark in Risk & Risk Management.Tags: Chris Mark, InfoSec, mark consulting group, Piracy & Maritime Security, privacy, risk management
add a comment
 Today on NBC Sports there was an article about woman rock climbing with her 2 year old strapped to her back. The toddler is not wearing a helmet. When asked she explained: “I can appreciate if you didn’t realize how safe the environment I was in, it could be worrying, but I was top-roping which means if you fall you don’t fall any further than where you came off.” She further opined: “It is the safest form of climbing you can do…Health and safety legislation and the sue and blame culture mean so many people are nervous, so afraid of getting into trouble, and taking small risks. Life is all about risks, whether that’s something as simple as getting in your car every day or climbing up a rock face.” This reminded me of a debate I had several years ago.
Today on NBC Sports there was an article about woman rock climbing with her 2 year old strapped to her back. The toddler is not wearing a helmet. When asked she explained: “I can appreciate if you didn’t realize how safe the environment I was in, it could be worrying, but I was top-roping which means if you fall you don’t fall any further than where you came off.” She further opined: “It is the safest form of climbing you can do…Health and safety legislation and the sue and blame culture mean so many people are nervous, so afraid of getting into trouble, and taking small risks. Life is all about risks, whether that’s something as simple as getting in your car every day or climbing up a rock face.” This reminded me of a debate I had several years ago.
I was talking with a company about protecting personally identifiable information (PII) as required by law. The company’s response was: “It is too expensive to comply. I will take the risk.” The problem lies in that the data that they are required to protect is not their information. While the data itself (bits and bytes) may belong to the company the information represented by the bits and bytes is the property of the person to which it refers. In short, it is not the company’s risk to assume as it is not their property. If I want to publish my own personal data on the Internet, I can do so and assume the risk…it is my data. A third party cannot assume risk for me…without my permission. This is why companies are required to protect PII, NPI, PHI, and other forms of personal data.
In much the same way this woman can free climb naked (alone) if she chooses. It is her risk to assume. Whether her style of climbing is the safest does not mean it is without risk. It is a less risky than free climbing but any form of rock climbing is an inherently risky activity. The 2 year old does not have the ability to state whether she wanted to climb or not. Where I have issue with the woman is her attitude of: “life is all about risks…” Granted but some peoples’ lives are about taking more risks than others. As adults we can make the decision to base jump, free climb, skydive, or race motorcycles. When we include others in our risky behavior without their consent, it becomes problematic.
