Chris Mark speaking on PCI at a Business Process Outsourcing (BPO) event 2013 June 29, 2014
Posted by Chris Mark in Uncategorized.Tags: AT&T, Chris Mark, compliance, compromise, data breach, DSS, hack, PCI, risk, security
2 comments
I was privileged to be able to speak at an AT&T BPO event in 2013. In Feb 2014 AT&T Marketing published the videos. I found one but was unaware they had published all 3. I hope you enjoy. (remember…the camera adds 10 lbs! 😉
Understanding Deterrence & Crime Prevention June 25, 2014
Posted by Chris Mark in Uncategorized.Tags: actor, Chris Mark, crime, criminal justice, deterrence, game theory, punishment, rational
3 comments
 This following an excerpt from the 2012 research brief titled “Failed State of Security; A Rational Analysis of Deterrence Theory and Cybercrime.” I was recently provided a blog post by an ‘expert’ in which the author was again blaming the victim of a data breach while chiding companies for believing that they should not expect law enforcement to be there when you need them. The author misses a major purpose of the criminal justice system; Deterrence of criminal behavior. I late 2013 a US Senator stood in front of a Target store and blamed Target for their data breach. Interestingly, this senator did not state that the US should redouble efforts to deter cybercrime through more effective laws or more aggressive law enforcement actions. Until the laws and criminal justice system can begin to deter such behavior, cybercrime will continue to plague data industries. So what is deterrence?
This following an excerpt from the 2012 research brief titled “Failed State of Security; A Rational Analysis of Deterrence Theory and Cybercrime.” I was recently provided a blog post by an ‘expert’ in which the author was again blaming the victim of a data breach while chiding companies for believing that they should not expect law enforcement to be there when you need them. The author misses a major purpose of the criminal justice system; Deterrence of criminal behavior. I late 2013 a US Senator stood in front of a Target store and blamed Target for their data breach. Interestingly, this senator did not state that the US should redouble efforts to deter cybercrime through more effective laws or more aggressive law enforcement actions. Until the laws and criminal justice system can begin to deter such behavior, cybercrime will continue to plague data industries. So what is deterrence?
An Overview of Deterrence Theory
Deterrence theory has applications in a variety of fields including military, and maritime security settings, foreign affairs, and in criminology, to name a few. While seemingly unrelated, when looked at closely, the similarities are apparent. Each these fields involve human decisions and humans that have the ability to behave and act in a manner contrary to the wishes of the other party. It is the ‘human element’ that is being modified by deterrent strategies.
History of Deterrence Theory
The concept of deterrence is relatively easy to understand and likely extends to the earliest human activities in which one early human dissuaded another from stealing food by employing the threat of violence against the interloper. Written examples of deterrence can be attributed as far back as the Peloponnesian War, when Thucydides wrote that there were many conflicts in which one army maneuvered in a manner that convinced the opponent that beginning or escalating a war would not be worth the risk.[1] In the 4th Century BC, Sun Tzu wrote: “When opponents are unwilling to fight with you, it is because they think it is contrary to their interests, or because you have misled them in to thinking so.”[2] While most people seem to instinctively understand the concept at the individual level, contemporary deterrence theory was brought to the forefront of political and military affairs during the Second World War with the deployment of nuclear weapons against Nagasaki and Hiroshima.[3] (more…)
Norse- Live Cyber Threat Intelligence (very cool!) June 24, 2014
Posted by Chris Mark in Uncategorized.Tags: attack, cyber, espionage, hack, IPViking, Norse, threat, vulnerability
add a comment
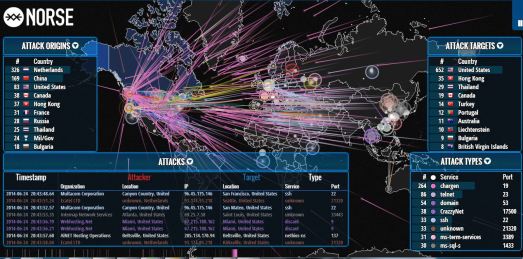
I have been thinking about a topic on which to write. I recently ran across this company called Norse and was impressed by the live cyber intelligence Norse provides. Please checkout their website…as stated: “Every second, Norse collects and analyzes live threat intelligence from darknets in hundreds of locations in over 40 countries. The attacks shown are based on a small subset of live flows against the Norse honeypot infrastructure, representing actual worldwide cyber attacks by bad actors. At a glance, one can see which countries are aggressors or targets at the moment, using which type of attacks (services-ports). “…forgive the language but this is…badass!
New Security Reference Blog…The Security HOG June 13, 2014
Posted by Chris Mark in Uncategorized.Tags: Chris Mark, compliance, risk, Scout Sniper, secuerityhog, security
add a comment
 Security HOG is a complement to the GlobalRiskInfo site but is solely focused upon providing insight and education on the concepts of security, risk and compliance. Having worked in numerous security domains for over 20 years has provided me with valuable insight into the concepts and underpinnings of the science and art of security. Whether we are talking about physical security, operational security, information security or cybersecurity, the basic concepts remain the same. This blog will focus on the more esoteric, yet important, concepts of proximate reality, deterrence & compellence, parallax and convergence, threats & vulnerabilities, risk, and more.
Security HOG is a complement to the GlobalRiskInfo site but is solely focused upon providing insight and education on the concepts of security, risk and compliance. Having worked in numerous security domains for over 20 years has provided me with valuable insight into the concepts and underpinnings of the science and art of security. Whether we are talking about physical security, operational security, information security or cybersecurity, the basic concepts remain the same. This blog will focus on the more esoteric, yet important, concepts of proximate reality, deterrence & compellence, parallax and convergence, threats & vulnerabilities, risk, and more.
Some might wonder what, if any significance, HOG has to the discussion of security? Within the USMC a person who is not a Scout/Sniper is known as a Professionally Instructed Gunman or PIG while a trained Scout/Sniper is known as a Hunter of Gunman or HOG. As a former Marine Corps Sniper I am a HOG and this is the reason the site is called Security HOG. Not too creative, I am afraid but it seemed to have a ring to it…