Black Swans, Probability Ignorance & FUD: Risk 101 February 13, 2012
Posted by Chris Mark in Risk & Risk Management.Tags: Chris Mark, InfoSec & Privacy, Maritime Security, mark consulting group, markconsultinggroup.com, Piracy & Maritime Security, risk management, security, security theater
add a comment
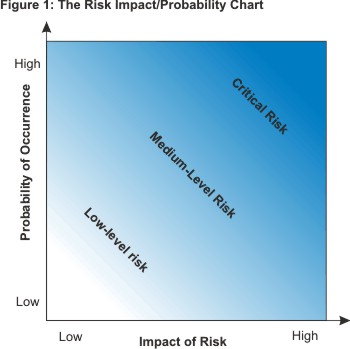 I have written several posts on risk and risk within the maritime security industry. You can read them here (#1, #2) There is a common mistake people sometimes make when venturing into risk management. It is the focus on the impact of an event while ignoring the probability or overestimating the probability of the event. Very serious events with very low probabilities of occurrence (or those which you are unable to calculate) are what has been coined as Black Swan events by Nassim Taleb in his book of the same name. When calculating or estimating risk it is sometimes a temptation to look at those incidents with high impact potential and low probabilities while ignoring the less severe events with her probability. This would be akin to venturing into the Amazon Rain Forest and protecting yourself from Grizzly bears (very large impact but low, low probability) only to die of blood loss from being bitten by a million mosquitoes because you did not take a mosquito net or bug spray as you were not concerned with “a little mosquito bite”.
I have written several posts on risk and risk within the maritime security industry. You can read them here (#1, #2) There is a common mistake people sometimes make when venturing into risk management. It is the focus on the impact of an event while ignoring the probability or overestimating the probability of the event. Very serious events with very low probabilities of occurrence (or those which you are unable to calculate) are what has been coined as Black Swan events by Nassim Taleb in his book of the same name. When calculating or estimating risk it is sometimes a temptation to look at those incidents with high impact potential and low probabilities while ignoring the less severe events with her probability. This would be akin to venturing into the Amazon Rain Forest and protecting yourself from Grizzly bears (very large impact but low, low probability) only to die of blood loss from being bitten by a million mosquitoes because you did not take a mosquito net or bug spray as you were not concerned with “a little mosquito bite”.
It is important to calculate risk by using a method that accounts for both impact and probability. This will give you a method by which to calculate the actual risk of an event and take appropriate steps to manage the risk. As can be seen by the graphic at the top of the post, a high impact low probability event poses the same risk as a low impact, high probability event assuming the ratios are equal. While the impact can be calculated as someone finite (for example, the worst that can happen to a person is likely to be killed) the probability of an event which can cause the event can range from unlikely to infinitesimally small. As an example of probability ignorance I will use an example from my own life. A woman I know carries a hammer in her car given to her by her mother. The purpose of the hammer is to break the car window and escape in the event the car plunges into a lake or other body of water and begins to sink. While the idea of drowning in a sinking car is certainly frightening, the likelihood of a car plunging into a body of water at 7,000 feet in high desert is very, very, very low. In this scenario it would be suggested that a better use of the money spent on the hammer was a 20 minute discussion on the value of always buckling the seatbelt and never speeding.
So why is this important? Simple. Security practitioners sell on a concept known as FUD or Fear, Uncertainty, and Doubt. A great example of FUD is a commercial I saw recently. A security company announced that 4 houses are burglarized every 14 seconds in the US. The commercial then goes on to show a mother and her children and how scary a burglary can be. Lets do some quick math to see how ‘scary’ this really is. According to the US Census Bureau there are about 131 million housing units in the US. If there is a house burglarized every 14.6 seconds this means that there are 4.1 burglarized per minute, 246 per hour, 5,917 per day and 216,000 per year. WOW! That is alot! BUT…this means that if you live in a home you have a .16% change of having your home burglarized in a given year. This does not seem so bad now. Keep in mind that some areas such as urban areas have higher crime rates than other areas and some houses are burglarized more than once. Another area where the security vendor attempts to convince you to use their services is by intimating that burglaries result in physical assault. In the commercials, a woman (not a man) is with her children talking about how the neighbor was burglarized and “while the children weren’t home, imagine if they had been.” Very few burglaries result in any physical harm to anyone but the imagery in the commercial is significant.
When listening to the inevitable sales pitch from a security vendor, keep in mind that they have an objective to sell you services. The easy way to do this is to use the FUD technique. If I am selling meteorite insurance, I will tell you about the dangers of meteorites, irrespective of who small they may be. Remember, it is easy to lie with numbers and easier to lie with statistics. Always base security implementation on a risk analysis.
Black Swan events – The Amazon rain forest example gives us a good opportunity to talk about Black Swan events. While we can calculate the probability of being attacked by a Grizzly bear in the Amazon (practically zero since they do not live anywhere but North America) there could be a situation in which a Grizzly bear was present and did attack someone. Maybe a person illegally imported a bear and let it go in the Amazon. This type of event would be a ‘Black Swan’ as you really could not calculate the probability of that specific event. The book is a very good starting point for this concept.
-Graphic from MindTools.com
InfoSec 101: Technology doesn’t fail, People do… January 27, 2012
Posted by Chris Mark in InfoSec & Privacy, Risk & Risk Management.Tags: access control, Chris Mark, data security, InfoSec & Privacy, Maritime Security, mark consulting group, policies, risk management
add a comment
 As research indicates that pirates are beginning to engage the services of data thieves to steal data from shipping companies, it is important that the maritime industry begin looking at securing not only their vessels but their data assets, as well. In my past life as a data security professional, I have had the opportunity to work with some very, large complex organizations. As a consultant I was often involved in the remediation and after action of companies that had experienced a data theft or major compromise (hack). After reviewing about 3,000 data compromise cases I can say with confidence that it is not the technology that fails in data compromises, it is the people. I have yet to ever see a firewall decide to stay home from work or decide to change its own ruleset to open a port. I have seen a number of instances where a firewall administrator forgot to close a port or bypassed the firewall for “just a minute” and forgot about the change. I have never seen an intrusion detection system (IDS) decide to turn itself off because it was tired, I have seen many instances where the IDS was tuned incorrectly, or where it was turned off because it was sending too many alerts. The scenario repeats over, and over. Technology doesn’t get tired, it rarely fails (statistically modern airliners are as reliable as toaster ovens) and it doesn’t complain, or make mistakes.
As research indicates that pirates are beginning to engage the services of data thieves to steal data from shipping companies, it is important that the maritime industry begin looking at securing not only their vessels but their data assets, as well. In my past life as a data security professional, I have had the opportunity to work with some very, large complex organizations. As a consultant I was often involved in the remediation and after action of companies that had experienced a data theft or major compromise (hack). After reviewing about 3,000 data compromise cases I can say with confidence that it is not the technology that fails in data compromises, it is the people. I have yet to ever see a firewall decide to stay home from work or decide to change its own ruleset to open a port. I have seen a number of instances where a firewall administrator forgot to close a port or bypassed the firewall for “just a minute” and forgot about the change. I have never seen an intrusion detection system (IDS) decide to turn itself off because it was tired, I have seen many instances where the IDS was tuned incorrectly, or where it was turned off because it was sending too many alerts. The scenario repeats over, and over. Technology doesn’t get tired, it rarely fails (statistically modern airliners are as reliable as toaster ovens) and it doesn’t complain, or make mistakes.
Human beings aren’t so fortunate. We are lazy by nature. I say this because we all will take the path of least resistance in everything we do. We are also fallible, which means we make mistakes. It is simply human nature. Unfortunately, in security this characteristic is why security breaches occur. A guard falls asleep. A firewall admin opens a port and forgets to close it. A janitor doesn’t lock a door after leaving a building. An employee forgets one step in a calculation. The list goes on and on. So how do we minimize the mistakes and mitigate the risk associated with human nature? The answer is simple but the implementation is difficult. Established processes and procedures documented in policy and…here is the hard part….. enforced.
I cannot tell you how many clients when asked if they have a security policy will say: “Well, we don’t have a documented policy…but we have an ‘informal policy’.” Wrong answer! If it is not formalized and approved by the appropriate authority (CIO, BOD, etc.) then it is NOT a policy…it is an informal practice. When I hear this answer I always ask: “How confident are you that the informal policy you describe is being followed?” The answer is inevitably: “well…probably not as frequently as it should be.” This describes the vast majority of companies I have worked with. Why? The answer is again simple. First, policies are difficult and time consuming to develop and implement. Second, we don’t like to step on other people’s toes. We want to trust our co-workers and employees. By establishing an onerous policy we are saying to them: “you are not trusted.” Lets call a spade a spade. None of us like being told we can or can’t do something or being treated like we are not trusted. Unfortunately in security it is absolutely imperative that we establish and enforce policies. Defined policies which are effectively enforced give us the only confidence that tasks are being conducted: “consistently, and repeatedly.” This is the key.
How do you develop policies and procedures? That topic is much to deep for this blog post but here is a high level process to follow.
1) Take an inventory of assets and prioritize those assets. (intellectual property, human resources records, financial data). You need to know what it is you are trying to protect before you can find a way to protect it.
2) Identify the who, what, where, why, when, and how of data access. Using the access control reports/system (Windows Active Directory, LDAP, etc.) and application information, identify the following: Who has access to the data (include applications, services and people), what data they can access, where the data is stored, why they have access (and whether they actually need access), when they have the ability to access (and whether it should be restricted) and how they access the data (direct SQL queries, applications, etc.) Develop a matrix with all info included.
3) Develop a dataflow diagram. Using the matrix above, and an existing logical network diagram, create a diagram that logically shows where all sensitive data (as identified in #1) is located and how it flows through the network (including all applications and devices). This process will be enlightening. Experiences suggests there will be a number of ‘ahaa’ moments where you find that people with no business need have access to very sensitive data.
4) Develop a ‘data control policy’ using model of least privilege and ‘need to know’. This is the first policy. Classify the types of data and decide who (people, applications, services) should be able to access which type of data, under what conditions (time, location, etc.) and provide a justification. This should be based on a ‘need to know’. For example, a system administrator (system level access) should not have access to the financial accounting database nor be able to see financial accounting data unless his/her job requires.
5) Update your access control mechanism to reflect the data control policy. Update user privileges and rights in Active Directory, or LDAP to reflect the data control policy. The Access Control Policy is another step that will be covered in another blog post.
By using the 5 steps above, you will be well on your way to controlling and protecting your sensitive data assets. Remember, policies are simply paper documents unless they are documented, approved by management, disseminated, and enforced. Although enforcement is often difficult, employees need to understand that violating information security policies can be met with punishment up to, and including, termination, OR prosecution.
PCI DSS and Piracy January 12, 2012
Posted by Heather Mark in PCI DSS, Piracy & Maritime Security.Tags: cybersecurity, Heather Mark, InfoSec, InfoSec & Privacy, Maritime Security, mark consulting group, PCI DSS, Piracy & Maritime Security
add a comment
 I’ve been reading quite a bit on piracy lately. Not the adventurous, swashbuckling tales of pirates flying down the Spanish Main, but piracy in its present form. From a purely detached perspective, its an interesting exercise in cause and effect. Natural disasters, for example, have an impact on the surge in piratical acts. The Christmas Tsunami left many Somali fishing villages devastated and took the last legal means of sustenance from many families that depended fishing for their survival. As a result, they turned to piracy. Of course, that is not to say that Somali pirates are the Jean val Jean’s of their day, the thief with the heart of gold doing only what is necessary to survive. These pirates are violent and aggressive and should not be coddled. The interesting comparison to the PCI DSS, in my mind, derives from the impact of the crime on the industry and the global reaction to the phenomenon.
I’ve been reading quite a bit on piracy lately. Not the adventurous, swashbuckling tales of pirates flying down the Spanish Main, but piracy in its present form. From a purely detached perspective, its an interesting exercise in cause and effect. Natural disasters, for example, have an impact on the surge in piratical acts. The Christmas Tsunami left many Somali fishing villages devastated and took the last legal means of sustenance from many families that depended fishing for their survival. As a result, they turned to piracy. Of course, that is not to say that Somali pirates are the Jean val Jean’s of their day, the thief with the heart of gold doing only what is necessary to survive. These pirates are violent and aggressive and should not be coddled. The interesting comparison to the PCI DSS, in my mind, derives from the impact of the crime on the industry and the global reaction to the phenomenon.
Impact of the Crime
Piracy is a crime that has an impact on all consumers. Higher insurance rates, security contingents, longer routes and therefore higher fuel costs, and similar circumstances that result from piracy mean higher prices for consumers. Any costs that cannot (or will not) be absorbed by the manufacturer or the shipping company are passed on to the consumer. Similarly, data thieves have very definitely left their mark on the consumer. Those of us involved in the electronic payment industry recognize better than most the increased cost structure that has resulted from trying to achieve and maintain compliance with the PCI DSS and the countless data security, data breach notification and consumer privacy laws at play in the United States. Ongoing compliance and security monitoring, evaluating the threat landscape and the cost of validating compliance can quickly add up for companies. Organizations that are already seeing their margins get squeezed are required to spend additional resources on security and compliance to ensure the safety of consumers’ data. Those costs can sometimes be passed along to the consumer.
Global Reaction
Data security and piracy were both issues that “flew under the radar” until high-profile instances brought them to the public awareness. In the world of transoceanic shipping, the issues that brought awareness were a couple of kidnappings for ransom and the hijacking of the Maersk Alabama. It’s important to note, however, that even before these incidents, the shipping industry and governments worldwide were working on standards and regulations that would mitigate the problem. The reaction from the industry should sound very familiar to veterans of the PCI DSS compliance world – “The standards are too prescriptive.” “The standards were written by people that don’t
really understand the issues.” “How are you going to ensure that everyone is complying with these standards?’ “The cost of complying with the standards are too burdensome for small companies.” These concerns should resonate with payment security professionals. The same questions and concerns are often raised about the PCI DSS.
For the payment industry, the events that really brought public awareness were a couple of high-profile data breaches at well-known retailers. The question really is, though, “What is the alternative?” If neither industry had done anything to address these growing issues, the constituents in the industry would have raised the alarm about the apparent lack of concern from the powers that be. The catch-22 of the creation and enforcement of the standards is that even though these standards achieve their objective of raising industry awareness and attempting to mitigate the risk of adverse events, the companies that suffer piracy attacks or data breaches are still often cast as the villian (as opposed to the victim) in the scenario.
What’s the Answer?
That is the crux of the matter – are the issues of data security and high seas piracy “solvable?” There are a variety of issues that drive the increase in both crimes. Economic stability, the ability of governments to project their authority into these areas, jurisdictional cooperation and other factors drive the growth of both types of crimes.
While I cannot confidently address permanent solutions to either problem, I can suggest a shift in perspective. In the realm of data security and payment security, practitioners often attempt to solve the problem by layering more and more technology in front of the sensitive data. Tokenization is one example of how a shift in perspective can provide alternative solutions. Extracting value from the data makes significantly less attractive to thieves. So instead of asking, “How can we keep thieves from accessing the data?” one might ask “What can be done in the transaction processing chain to render the data unusable to thieves?” We are currently retro-fitting security onto a system that has been in place for fifty years. If we were to remove any preconcieved notions of what a payment infrastructure should look like, what would we design?
Roque Wave; Secure Payments Article January 11, 2012
Posted by Chris Mark in InfoSec & Privacy, Laws and Leglslation.Tags: Chris Mark, InfoSec, InfoSec & Privacy, mark consulting group, markconsultinggroup.com, PCI, PCI DSS, risk management, roque wave, secure payments, security
add a comment
This is an excerpt from an article I wrote a couple of years ago called “The Rogue Wave”. It discusses a high level overview of Doctrine, Tactics and Strategy and applying PCI DSS as doctrine…You can read the full article here.
“Recent data compromises have continued to illustrate the challenges of securing data in an increasingly hostile environment. Companies are faced with securing and protecting their valuable information form a growing number of increasingly sophisticated and organized groups determined to steal valuable data. Historically, the response to data compromises has been to pass and enforce increasingly strict standards, regulations, and laws detailing the specific steps companies must take to protect data and the required disclosure should data be compromised. Those companies that are the unfortunate victims of data thieves are criticized and vilified for “losing data”. In spite of the efforts being focused upon compliance with the various laws and standards, data compromises continue in their steep upward trend seemingly unabated…”
Chris Mark in The Maritime Executive August 30, 2011
Posted by Chris Mark in InfoSec & Privacy, Piracy & Maritime Security, Risk & Risk Management.Tags: Chris Mark, cyber piracy, InfoSec, InfoSec & Privacy, Maritime Security
add a comment
 Yours Truly (Chris Mark) was interviewed in the current issue (July – August, 2011) of The Maritime Executive on the topic of Cyber Piracy. You can read a summary of the issue here. If you are not a current reader, Maritime Executive is a great periodical with volumes of information on the Maritime industry. You can subscribe to the print edition here.
Yours Truly (Chris Mark) was interviewed in the current issue (July – August, 2011) of The Maritime Executive on the topic of Cyber Piracy. You can read a summary of the issue here. If you are not a current reader, Maritime Executive is a great periodical with volumes of information on the Maritime industry. You can subscribe to the print edition here.
“Jack O’Connell has explored the Internet underworld with his piece, “Cyber Piracy: Clear and Present Danger?” It’s a dangerous cyber world in which we unknowingly tread, so users beware. Both of these article’s are timely and essential reminders of an Internet moving faster than a speeding bullet.”
