Oil Giants Hacked by Anonymous in “Save the Arctic Phase2” July 16, 2012
Posted by Chris Mark in Data Breach, Industry News.Tags: anonymous, bp, cybercrime, cybersecurity, data breach, exxon, InfoSec & Privacy, mark consulting group, savethearctic, security
add a comment
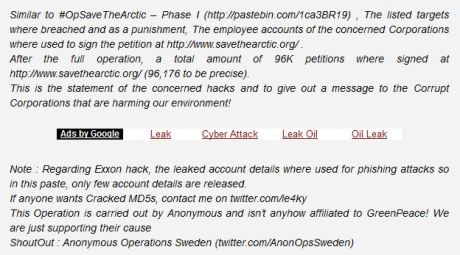
 According to CyberWarNews.com Anonymous set its sites on oil giants Shell, BP, Gazprom, and Rosneft in what has been dubbed “Save the Arctic Phase 2”. This comes on the heels of phase one in which account details including administrator accounts, passwords and other server info was stolen from Exxon and released.
According to CyberWarNews.com Anonymous set its sites on oil giants Shell, BP, Gazprom, and Rosneft in what has been dubbed “Save the Arctic Phase 2”. This comes on the heels of phase one in which account details including administrator accounts, passwords and other server info was stolen from Exxon and released.
According to the messages posted on pastebin, the account were used to sign the petition on savethearctic.org and, more disturbingly, for phishing attacks. Hacktivism is a growing concern for all companies. Whether it be to combat the perceived unfair distribution of wealth of capitalism, support of US defense industry, or environmental issues, hacktivists are increasingly active against corporations.
“Are You Eating a Rotten Apple?” – Personal Data May have Been Exposed in Global Payments Breach July 9, 2012
Posted by Chris Mark in cybersecurity, Data Breach, Industry News, InfoSec & Privacy, PCI DSS, Risk & Risk Management.Tags: compliance, cybersecurity, data breach, Global Payments, mark consulting group, PCI DSS, PII, risk management, security
add a comment
 Let me preface this post by saying this is not intended to take shots at either Global Payments or the PCI DSS. Rather, this post is intended to generate discussion and discourse on the topic of compliance and risk management.
Let me preface this post by saying this is not intended to take shots at either Global Payments or the PCI DSS. Rather, this post is intended to generate discussion and discourse on the topic of compliance and risk management.
According to reports, it seems that the Global Payments data breach may have exposed more than payment card data. n a June 12 update posted to its breach microsite, Global says hackers may have gained access to servers containing personal information collected from a subset of merchant customers.
“The company will notify potentially affected individuals in the coming days with helpful information and make available credit monitoring and identity protection insurance at no cost,” Global says. “The notifications are unrelated to cardholder data and pertain to individuals associated with a subset of the company’s U.S. merchant applicants.”
Based upon this statement it seems fair to assume that Personally Identifiable Information (PII) such as Social Security number and Bank Account information may have been exposed, as well.
This situation exposes the danger of using a narrowly focused, static standard as a baseline of security management rather than adopting a risk based approach to data security. I have personally conducted over 100 PCI DSS audits and have seen first hand the resources consumed by the standard. Companies often appear so laser focused upon protecting payment card data that other systems and data may take a back seat in the pursuit of “PCI DSS compliance.” As there are significant penalties associated with non-compliance that it is difficult to blame the merchant or service provider. The penalties are designed to compel compliance with the standard. As such, companies are going to give precedent to the PCI DSS over any other standard that does not have equivalent penalties associated with non compliance.
As a reminder, the PCI DSS is ONLY focused protection of Cardholder Data. Surely some are going to say that the PCI should be applied across all systems etc.etc. This is great in theory but does not happen in practice. Companies take great pains to minimize their cardholder data environment specifically to lessen the compliance burden.
I am sure we will continue to see breaches of payment card companies having PII exposed as companies focus on PCI to the exclusion of risk based security management.
“Let’s Talk Data Security” – Heather Mark in July 2012 Greensheet & TransactionWorld July 9, 2012
Posted by Chris Mark in cybersecurity, Data Breach, Laws and Leglslation, News, PCI DSS.Tags: cybersecurity, data breach, data security, greensheet, Heather Mark, mark consulting group, security, transactionworld
add a comment
 Heather Mark is interviewed in the July 2012 issue of Greensheet in the article titled: “Expert Advice on Security Defense and Planning”. The article discusses strategies for preventing and dealing with data breaches with the payment card industry. Additionally, Heather has an article in TransactionWorld titled: “New School vs. Old School: Security and Emerging Technologies”. You can catch Heather’s articles every month in Transaction World Magazine.
Heather Mark is interviewed in the July 2012 issue of Greensheet in the article titled: “Expert Advice on Security Defense and Planning”. The article discusses strategies for preventing and dealing with data breaches with the payment card industry. Additionally, Heather has an article in TransactionWorld titled: “New School vs. Old School: Security and Emerging Technologies”. You can catch Heather’s articles every month in Transaction World Magazine.
Oh My!! More than 6 Million LinkedIn Passwords Stolen! June 6, 2012
Posted by Chris Mark in cybersecurity, Data Breach, Industry News.Tags: Chris Mark, cybercrime, cybersecurity, InfoSec, LinkedIn, privacy, security, Stolen Passwords
add a comment
 Change your LinkedIn password now! According to an article on CNN, over 6 million LinkedIn passwords were stolen by Russian hackers. LinkedIn also confirmed in their own blog post that some of the posted passwords did match LinkedIn accounts. According to the story: “The 6.5 million leaked passwords were posted Monday on a Russian online forum, camouflaged with a common cryptographic code called SHA-1 hash. It’s a format that’s considered weak if added precautions aren’t taken. Roughly half of the “hashed” passwords have already been decoded and posted online in human-readable text.” You can read more about how Hashes are cracked using Rainbow tables in the awesome post here.
Change your LinkedIn password now! According to an article on CNN, over 6 million LinkedIn passwords were stolen by Russian hackers. LinkedIn also confirmed in their own blog post that some of the posted passwords did match LinkedIn accounts. According to the story: “The 6.5 million leaked passwords were posted Monday on a Russian online forum, camouflaged with a common cryptographic code called SHA-1 hash. It’s a format that’s considered weak if added precautions aren’t taken. Roughly half of the “hashed” passwords have already been decoded and posted online in human-readable text.” You can read more about how Hashes are cracked using Rainbow tables in the awesome post here.
“Kiss My QR Code”; Symantec Releases 2011 Internet Security Threat Report May 20, 2012
Posted by Chris Mark in cybersecurity, Data Breach, InfoSec & Privacy.Tags: Chris Mark, cybercrime, cyberespionage, cybersecurity, Internet Threat Report, malware, Phishing, QR Code, Symantec
add a comment
 This month Symantec released the results of their 2011 Internet Security Threat Report. It is a very compelling read and highlights just how difficult it is becoming to protect systems, and data. Some of the more interesting findings: 2011 saw variants of Malware increase from 283 million to 407 million (you read that correct…million). Additionally, data thieves have begun using QR codes to infect Android phones with malicious software. One out of every 299 emails is a phishing attempt. This is a document that I recommend you download and read.
This month Symantec released the results of their 2011 Internet Security Threat Report. It is a very compelling read and highlights just how difficult it is becoming to protect systems, and data. Some of the more interesting findings: 2011 saw variants of Malware increase from 283 million to 407 million (you read that correct…million). Additionally, data thieves have begun using QR codes to infect Android phones with malicious software. One out of every 299 emails is a phishing attempt. This is a document that I recommend you download and read.